VPNクライアントからの接続
クライアントソフト
「vpnux Client」を使用してみます。管理者権限が必要なく、使用もとても簡単なので…。
OpenVPN for Androidのインストール
OpenVPN for Androidのプロファイル登録
事前にsdカード等で「ca.crt」「client1.crt」「client1.key」「ta.key」を準備します-
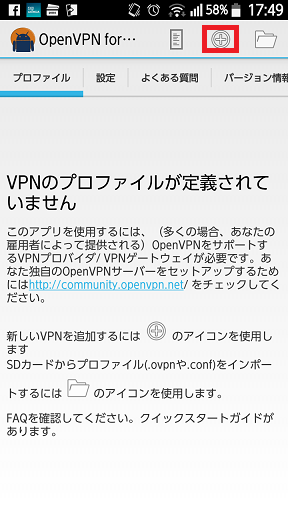
OpenVPN for Androidの起動画面です。
+を押してプロファイルを作成します。
-
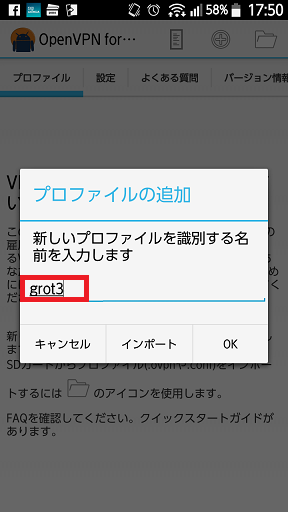
プロファイル名を入力します。
-
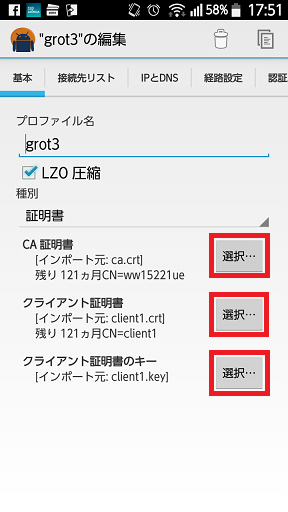
種別:証明書を選択します。
「ca.crt」;「client1.crt」;「client1.key」をそれぞれ選択します。
-
サーバーIP(もしくはサーバー名)を入力します。
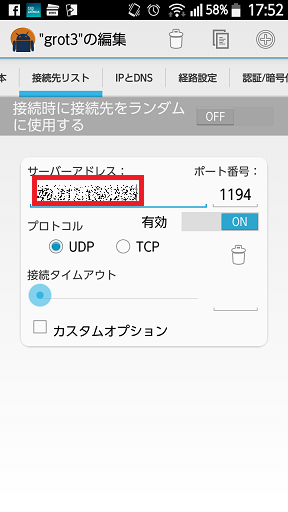
-
デフォルトのままです。
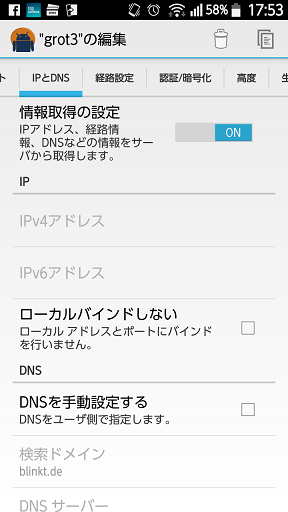
-
デフォルトのままです。
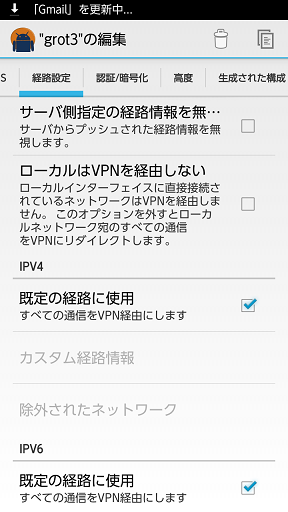
-
「TLSサーバー証明書を要求する」にチェックを入れ、TLS認証ファイルを選択します。
※「証明書のホスト名を確認する」は、ca.crt作成時に適当に入れた場合、チェックを外してください。
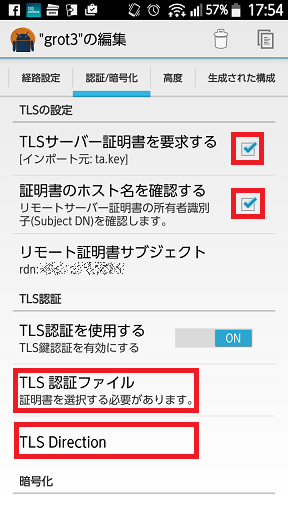
-
「TLS Direction」を"1"にします。
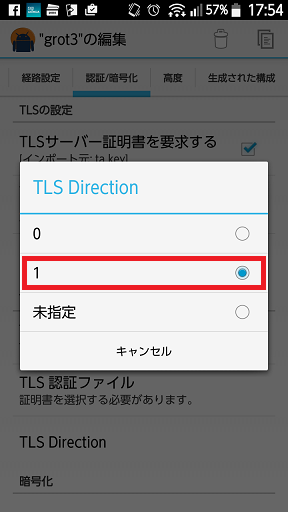
-
起動します。
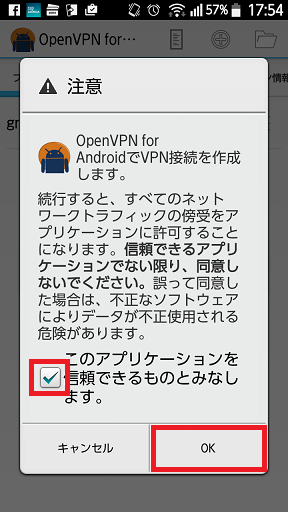
-
起動中の画面です。
メッセージが表示されていますが、最終行に「Completed」が表示されればOKです。
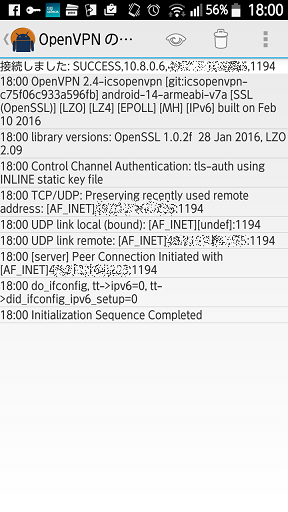
-
openvpnサーバー上のログです。
※接続元IPアドレスは「XXX.XXX.XXX.XXX」に手直ししてあります。
Sat Feb 27 18:00:58 2016 client1/XXX.XXX.XXX.XXX:1024 TLS: new session incoming connection from [AF_INET]XXX.XXX.XXX.XXX:1024
Sat Feb 27 18:00:58 2016 client1/XXX.XXX.XXX.XXX:1024 CRL CHECK OK: CN=grot3.com
Sat Feb 27 18:00:58 2016 client1/XXX.XXX.XXX.XXX:1024 VERIFY OK: depth=1, CN=grot3.com
Sat Feb 27 18:00:58 2016 client1/XXX.XXX.XXX.XXX:1024 CRL CHECK OK: CN=client1
Sat Feb 27 18:00:58 2016 client1/XXX.XXX.XXX.XXX:1024 VERIFY OK: depth=0, CN=client1
Sat Feb 27 18:00:58 2016 client1/XXX.XXX.XXX.XXX:1024 Data Channel Encrypt: Cipher 'BF-CBC' initialized with 128 bit key
Sat Feb 27 18:00:58 2016 client1/XXX.XXX.XXX.XXX:1024 Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Sat Feb 27 18:00:58 2016 client1/XXX.XXX.XXX.XXX:1024 Data Channel Decrypt: Cipher 'BF-CBC' initialized with 128 bit key
Sat Feb 27 18:00:58 2016 client1/XXX.XXX.XXX.XXX:1024 Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Sat Feb 27 18:00:58 2016 client1/XXX.XXX.XXX.XXX:1024 TLS: move_session: dest=TM_ACTIVE src=TM_UNTRUSTED reinit_src=1
Sat Feb 27 18:00:58 2016 client1/XXX.XXX.XXX.XXX:1024 TLS: tls_multi_process: untrusted session promoted to semi-trusted
Sat Feb 27 18:00:58 2016 client1/XXX.XXX.XXX.XXX:1024 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 DHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
Sat Feb 27 18:00:59 2016 client1/XXX.XXX.XXX.XXX:1024 PUSH: Received control message: 'PUSH_REQUEST'
Sat Feb 27 18:01:04 2016 client1/XXX.XXX.XXX.XXX:1024 PUSH: Received control message: 'PUSH_REQUEST'
Sat Feb 27 18:01:04 2016 client1/XXX.XXX.XXX.XXX:1024 send_push_reply(): safe_cap=940
Sat Feb 27 18:01:04 2016 client1/XXX.XXX.XXX.XXX:1024 SENT CONTROL [client1]: 'PUSH_REPLY,route 10.8.0.1,topology net30,ping 10,ping-restart 120,ifconfig 10.8.0.6 10.8.0.5' (status=1)
メモ: